Overview
In a complex world of ever-evolving technologies,Nexus Controlsunderstandsthe importance of having an experienced industrial cybersecurity partnerto help you safely secure your digital assets.
As a leading provider ofoperational technology cybersecurity solutions for more than a decade, Nexus Controls is well-equipped toenhance the security postureof your enterprise,achieve greater visibilityto protect critical assets, andsupport internal and external compliancepolicies and requirements.
With the application whitelisting option, Windows®-based devices havean improved security posture by reducing the risk and cost of malware, improving network stability and reliability.
This featureautomatically identifies trusted software that is authorized to run on control system HMIs and prevents unknown or unwanted software.

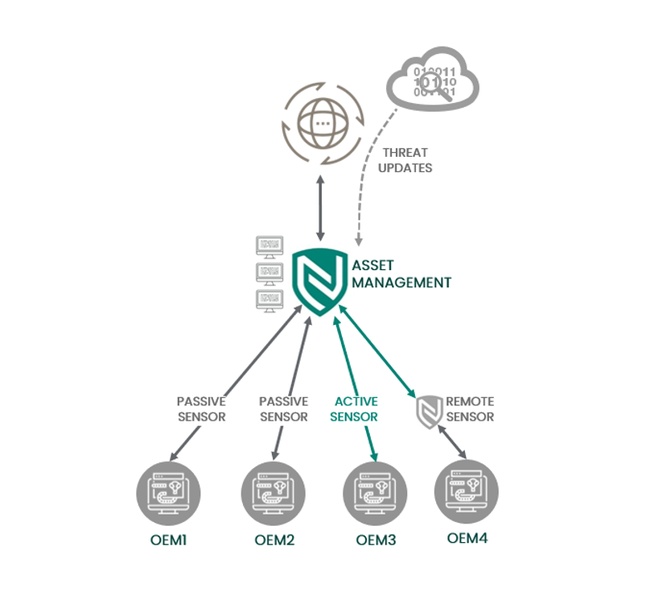
Continuous threat monitoringandadvanced logging intelligencethat gives you deep, granular ICS visibility. Byanalyzing network trafficthrough deep packet inspectionandfluent in over 42 of the native industrial protocols commonly found in ICS security, a baseline is constructed of normal operations which is thenused to detect anomalies.
Asset Identification
- Identify and list the assets present on the networks monitored
- Identify information such as make, model, firmware, Operating System, installed software
Asset Configuration Change Detection
- Identify if a change has occurred over the network or to the devices on the network which may indicate a compromise
- Identify if a change has occurred to an industrial device which may be an indicator of a compromise
Methods of Discovery
- Active discovery
- Passive discovery
- Hybrid discovery
Automatic, centralized backup and recoveryof the process control domain saves time and cost bydeploying a quick disaster recovery planwith minimal downtime.
All backup activities arelogged and easily accessed for generating reportsthat conform with compliance reporting.

Ahardware-based electronic device designed with two separate circuits -one send-only, and one receive-only - which physically constrain the transfer of data to one direction only and form an “air gap” between the source and destination networks.
A data diode is a physical piece of hardware thatacts as a unidirectional network communication device that facilitates a secure, one-direction transfer of data between networks.Their design inherently creates a physical separation between the source and destination networks. Data diodeseffectively eliminate any and all external points of entryto the sending system, thus preventing unauthorized users the ability to gain access to the protected network.
By securing a network's data outflow,data diodes make it impossible for any third party to inject malware, access your system, or make any harmful changes to your network.
Data diodes can be used toprotect network segments of all sizes, from a single controller to an entire facility.

Thiscustomizable network security optionmonitors and blocks malicious activity and attacks andprovides continuous visibility of unusual activity and potential threatsto the control system network.
Stateful tracking of network traffic to allow approved communications between connected devices and the “outside” network. In addition,Next Generation Firewalls can inspect certain network traffic typesto identify ports that may change during communications to ensure traffic is permitted to flow (e.g. FTP, TFTP).
Next Gen Firewalls have the ability toperform additional checks on traffic including application-level inspection and filtering of network traffic with exception.
Network Intrusion Detection and Prevention Systems Factsheet

Patching your systems isone of the essential first steps to take to protect your assetsand assure the operating systems and programs running have updates to provide the latest security protection without risking your operation.Listed as two of the “First Five Quick Wins” by The SANS Institute, a well-respected authority on information security and cybersecurity training,patching of application and system software is criticalto improving and maintaining a high-security posture.
TheCyber Asset Protection subscription provides monthly software and firmware updatesfor your HMI, historians, switches, firewalls, OSM and RSG, including essential security patches. With Nexus OTArmor, patches can be centrally deployed, eliminating an average of four hours per HMI of work hours, which can save up to $20,000 monthly per plant.

Providescentralized control and management specific to the controls environment, enabling you to manage access to the industrial control system based on permissions. Benefits of RBAC include:
Increased Oversight for Admins -RBAC gives admins and managers deeper visibility and greater oversight, while also controlling authorized users and guests on the system so that they are only given access to what they need for their respective roles.
Lower Risk -By implementing RBAC, you have inherently restricted access to sensitive information while simultaneously creating logs of access for those with proper permissions, thus greatly reducing your risk of a data breach.
Cost Reduction -By restricting a user's access to certain processes and applications, admins can effectively conserve their key system resources such as bandwidth, memory, and storage.
Enhanced Operational Efficiency -By employing an effective RBAC strategy, organizations can decrease the need for password changes when onboarding new hires or when a user has to switch their role within the organization. RBAC lets you quickly add and change user-defined roles, while greatly reducing the time and resources needed to implement these roles across platforms, operating systems, and applications. Additionally, RBAC allows organizations to easily integrate outside, third-party users into their networks by assigning them predefined roles specifically designed for contractors and the like.
Improved Compliance -Every industry has its own governmentally mandated standard for compliance. Most organizations prefer to implement RBAC systems to meet the regulatory and statutory requirements, thus allowing their IT departments to more effectively manage how their data is accessed and used. This is particularly important for power providers and their supporting plants/locations where unauthorized access to their networks represents a significant threat that manage sensitive data.

We provide ascalable solution with both real-time and historic dashboard views of cyber activity, such aschanges to switch configurations, failed login attempts, unauthorized port access, and USB usage.
Operator Cybersecurity Dashboards
- Nexus Controls designed dashboards
- Data-rich Security Incidents & Events Management (SIEM)
- 准备好安全操作中心(SOC) integration
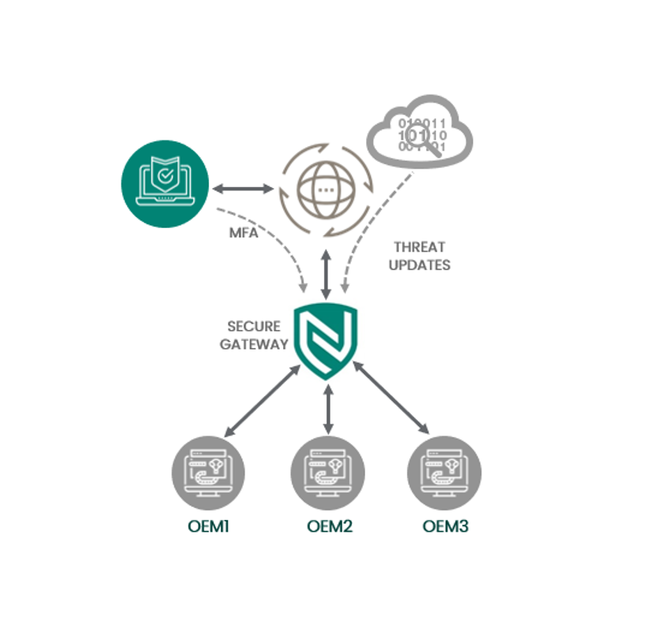
Adoptingstronger employee and vendor authenticationis an easy method to reduce risk.
Multifactor Authentication (MFA), sometimes referred to as two-factor authentication or 2FA, is a security protocol thatrequires a user to present two pieces of evidence when logging in to a given account or application. The most common example of multifactor authentication you'll typically encounter is when looking into your personal bank account. You will have one set of authenticators, your username and password for the site/app, and a second set of authenticators, usually by means of a separate device, i.e. your phone, where you will be sent a one-time code that must be entered into your banking site/app in order to proceed. This exponentially reduces the risks associated with brute force and stolen credential attacks as this 2FA protocol requires access to a separate device, and the window for authentication is typically pretty short.
Multi-factor authenticationcombines hardware-based authentication and public key cryptographyto ensure strong authentication and eliminate account takeovers.

Azero-trust solutionthat safeguards against cyber risks, including insider threats, through its unique, browser-based hardened platform. Secure remote access technologyprovides a simple and secure access mechanismto critical assets by utilizing protocol and system isolation, encrypted display, and multi-factor authentication.
Benefits include:
- Multi-Factor Authenticationencrypted remote access
- Secure gateway usingZero Trustsecure access solution
- Video replay technology formaximum isolationbetween plant operation assets and external remote access users
- Granular access control mechanisms andmediated remote file transfer
- Protect against zero-day malwareutilizing advanced malware detection
- Simultaneous user access, ideal for awork-from-homeenvironment
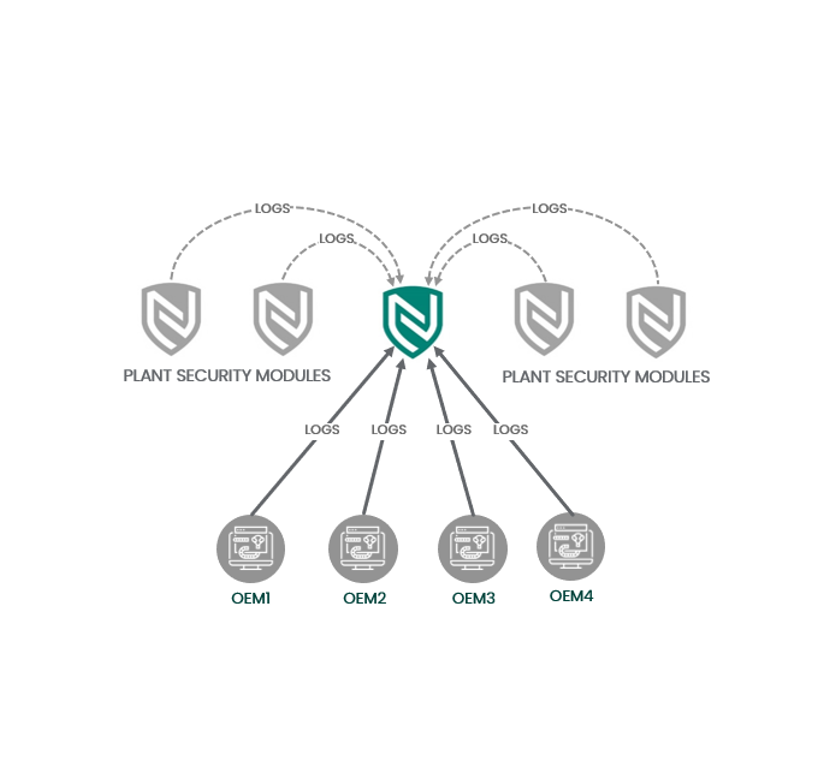
Nexus Controls’ team of cybersecurity analysts areexperts in big data solutions like, Elastic Search, Splunk & Hadoop.These highly skilled forensic analystsreview relevant logs to minimize false positives and maximize detection of threats.
Whether you already have a Security Operations Center (SOC) or not,our 24X7 managed security services are scalable to meet your unique needs.
- Industrial process control experienced
- Ingest relevant logs to minimize false positives to maximize detection and forensics
- Expert system assists analysts for human evaluation of most important threats
- 24x7 operations, geographically distributed
- Full integration with holistic threat intelligence (not just another feed)
- Human-Led, OT/IT technology accelerated

Cyber Asset Protection (CAP) is a key part of a defense-in-depth system for turbine, plant, and generator controls environments. The patching program includes operating system and application patches as well as anti-virus/ intrusion detection signatures to cover updates for HMIs, servers, switches, and network intrusion detection devices. Monthly updates can be applied to individual HMIs or via the NexusOTArmor™平台network-wide deployment.
How it works:
The Cyber Asset Protection subscription provides monthly updates for your HMI, data historians, switches, firewalls, OSM and RSG. Software updates include:
- Microsoft Windows® operating system
- Intrusion detection signatures
- Anti-virus signatures
- Switch firmware updates, when impacted by a security vulnerability
The CAP subscription service also provides a monthly report of patches that need to be installed and the areas of which are critical for attention. Only the necessary patches are provided. Installing unnecessary patches, such as those coming directly from Microsoft, can increase the risks to the plant.
Benefits:
- Provides tested updates to keep your legacy critical infrastructure current
- Reduces downtime by providing only the necessary validated patches which are tested in an environment to assure applicability and compatibility
- On a monthly basis, CAP keeps your risk profile updated and increasingly improves your security posture, by protecting your critical assets from known vulnerabilities
- Helps you meet regulatory requirements and avoid fines
- Improves safety and reliability by preventing loss of view
- Provides a dedicated service manager for cybersecurity issues

Cybersecurity assessments:
Nexus Controls provide a large variety of security assessment services. They are designed so the CEO, CISO, Plant Manager, or Compliance Manager to prioritize steps for mitigation, and even to help obtain future budgets within a multi-year cybersecurity program. Types of Assessments offered include:
- CIS Top 20 Controls
- Highly complex risk assessments or Penetration tests
- Product security assessment (IIOT, Controller, etc.)
- Compliance gap (NERC, NEI, IEC, etc.)
- Adversary Emulating Red Team Engagements
- Hunting as a Service (HaaS)
- Credential Risk Assessment
- Network Architecture Assessment
- Threat Risk Assessment
- Vulnerability & Risk Assessment
The other professional services that Nexus Controls offers include:
- Cybersecurity Profiling
- Industrial Wireless Network Services
- Cybersecurity/Compliance audits
- Incident Response Planning
- 事件响应:现场服务
- Forensics & Analysis services
- Tabletop exercises (TTX)
- Virtual CISO
- Prioritized Security Roadmap
- Advanced security consulting (Ex. architecture review)
- Building the governance model and procedures (network security governance)
IEC 62443-2-4(maturity level 2) certification ensures secure lifecycle of NexusOTArmoras an integrated system. This ensures safe industrial operations through a detailed analysis of our engineering processes throghout the security lifecycle; product design, manufacturing, network and system security, installation, and commisioning.
IEC 62443 3-3(security level 3) certified industrial cybersecurity platform that ensures that the NexusOTArmorcybersecurity solution was engineered utilizing a secure product development lifecycle process that includes IEC defined functionality and maintainable security. Additionally, this certification validates that the NexusOTArmor安全内核的组合进行了严格的测试ity risks.
These important industry certifications demonstrate our commitment to protecting industrial customers, including assisting them with regulatory and compliance requirements including NERC, NEI 08-9, CIS and NIST.